Cyber Security NZ
Protect yourself, your information & your organisation with Kinetics Group
Cyber Security Services

Don't wait
Hackers are circling – and getting smarter all the time. We’re ready to help you with a solution that meets your needs, and to get you locked down and safe quickly. We help you protect your Clients, Data, Private information, Identities, Financial information, Operational uptime and Reputation.
Book your free assesment with us now!
Choose a protection level:
Cyber Security Foundation
Including EDR, Security Awareness Education, Phishing Tests, MFA Management, DNS Filtering/Scrubbing, Shadow IT detection and more.
THE MINIMUM LEVEL SECURITY MEASURES ORGANISATIONS SHOULD BE TAKING.
Cyber Security Plus
Foundation plus Vigilance 24/7 EDR and Active Monitoring, 365 Online Backup, Password Vault, Data Leak Protection, an extra layer of email scrubbing, Breach Activity Scans and Deep Vulnerability Scans.
IF YOUR ORGANISATION RELIES ON DATA FOR ONGOING OPERATION OR REPUTATION, YOU SHOULD HAVE SECURITY PLUS.
Both Kinetics KARE cyber security plans include a pack of services that help keep your information in, and cyber breaches out! Your data is precious and should be treated as such. The main issue with protecting information is that you can’t lock it away because you need to use it to operate.
With both plans, not only does Kinetics provide protection software, but also education for your staff so they can actively work in the safest way possible and know how to identify potential risk to your organisation. Kinetics will also test them and present you the findings, so no one gets left behind on the security front. From blocking harmful websites, to scanning emails and deep scanning with antivirus, Kinetics has you covered when it comes to cyber security services in NZ.
If you are looking for the best level of protection, the Security Plus plan provides a much deeper level of cyber security, with endpoint protection and response which alerts users to the risks of a downloaded attachment, disconnects any infiltrated devices from the network you are using, assists with the prevention of internal attacks and help organisations align with insurance compliance for a full circle or protection. Plus is the technical support that you need, when you need it, not an app or extension that has been downloaded as a cheap solution to security that has no professional on the other end overseeing security or data privacy issues.
And potentially, most important of all;
Kinetics Security Plus plan provides managed password solutions, so your staff don’t make the all-too-common error of creating easy to guess passwords and never changing them. KARE Password Vault is customised to each business and means not even Kinetics can see into your passwords, or your employees.
Still not sure what plan is best for you? Contact Us here, we’d be happy to help give you the cyber security service you need!
Download our latest executive “10 minute” briefing to share with colleagues

Read some of the latest news on Cyber-Security
What would you do?
Imagine – you are busily going about your day when suddenly your meeting is interrupted. “No one can access their files!!!” or “We just accidently paid $50,000 to a fraudulent account and we can’t get it reversed!!!” or something similar. What would you do? Where...
Security Updates
We need to make some security changes. These are in accordance with the continued work by Microsoft to protect 365 users. This will keep your configuration current with their latest advisories but may have some (limited) impact on your IT experience. It is all about...
Layered Security Works
There is no silver bullet in cyber-security. Best practice requires layers of protection. One of those layers is ‘geo-blocking’, which means you can only log in from specified countries and overcomes many of the African and Eastern European hacker fraternities....
Look out for LinkedIn Smart Links
This is a great example of needing new tools that didn't used to exist, to keep cyber-safe, even if they add cost to our cyber-protection. Hijacking your trust in LinkedIn Cybersecurity firm Cofense have detected phishing campaigns that used LinkedIn links called...
Would your cyber-security have saved you from this hack attempt?
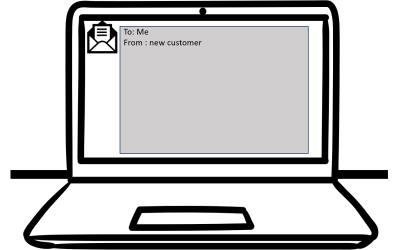
This is a real and very clever 'spear-phishing' attempt that one of our legal clients in Auckland received today.Would you have opened it? Would your IT have protected you?To: Me From : new customer Hello, My Husband and I are looking to buy a property (First-time...
Is it really you?
News that an elderly woman was tricked out of $100,000 over Facebook won't be a surprise to regular readers. She was fooled into thinking she was talking to a friend, and then sending money to access some make-believe Covid fund. AI makes it easy to speak in...
Ransomware claims increase 27%
The Coalition Insurance "2023 Cyber Claims Report: Mid-year Update" highlights the changing nature of the cyber threat landscape that businesses are currently facing, with a record surge in claims severity compared to the previous year. This is US data but it tends...
Webinar Replay : Learn How to Protect Yourself from the Darkweb Now
What does it mean If your personal details are leaked on the darkweb? Learn how you can manage your risks.The darkweb is a network of websites and servers that are not indexed by traditional search engines and require special software to access. It's a place where...
Protect Yourself from AI Phone Scams: A Terrifying New Trend
The rise of AI phone scams has brought personal targeting to a whole new level. Scammers are using AI-created fake texts (smishing) or even AI -created cloned voices of social media users. It has already found its way to New Zealand shores - New AI combats text...
KARE – Will your support plan need to change?
2008 was a long time ago. New Zealand was a different place. The IT maintenance needs of business were so much simpler! Locally, there was a change of government. Internationally, we were watching the start of the GFC with the fall of Lehman Bros bank. In the...