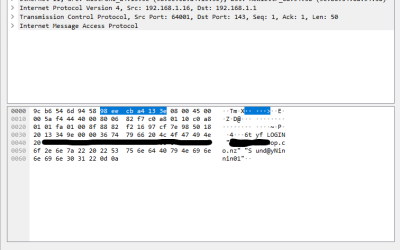
Data Leak Protection (DLP)
is the name of several policies in Office 365, setting up what data can, and can’t be, shared and with whom.
Imagine being able to automatically identify private information like passport numbers, Health IDs or bank account details and make sure that those are only being shared with people that are authorised to see them.
The good news is that you can do this with 365, provided you turn on the policies and set them up correctly, and monitor when data is shared.
Under the NZ Privacy Act, we’re all expected to take care of personal data entrusted to us and to make sure it’s only used for the purpose for which is being obtained.
With Office 365, there’s no excuse for that to be breached provided that we understand what data should be kept, what might be kept incorrectly, and how its being shared. With this we can set up rules to monitor your Office 365 system and report on how records are shared.
We include a basic set up of DLP in our KARE for Security S2 plan to get you started.

Will some of your emails stop?
Microsoft Exchange Online to retire Basic authentication We are going to face a big change coming in September 2025, Microsoft is going to be disabling SMTP Basic Authentication. This continues work they commenced a couple years ago to disable other protocols such as...
How to create passwords that hackers hate
A guide to making your online accounts more secure and less boring Have you ever used your birthday, your pet's name, or the word "password" as your password? If so, you're not alone. According to a study by NordPass, these are some of the most common and worst...
Is MFA enough? – the need for multiple cyber security layers.
At Kinetics, we've always emphasized the importance of multi-factor authentication (MFA) as a critical layer in cybersecurity. Without MFA, it's only a matter of time before you fall victim to a cyber attack. However, as we've also mentioned, no single defense is...
Securing your Mac
It does not seem that long ago I would hear Mac users say “I don’t need Anti-Virus”, or "Mac’s are not affected". To a certain extent they were right. Apple's use of tightly controlled application approvals reduced the surface area for attack. Mac users did not enjoy...
How secure is your cloud IT? Is it as safe as you expect?
Your cloud computing can be safe and secure, or open and vulnerable - the choice is yours. With the rise of hacker activity and cybercrime, it’s essential to lock down your cloud and protect it from threats. For most businesses, the standard 365 settings aren't...
What would you do Canterbury? Incident Response Workshop
Mastering Cybersecurity What would you do? Table-top exercise Join us for an interactive table-top simulation exercise. Imagine - you are busy going about your day when suddenly your meeting is interrupted. "No one can access their files" or "We just accidently paid...
Are your legacy IT systems giving hackers a backdoor into your business?
One of our engineers was working on migrating a customer from a legacy email server into Office 365 after we discovered they were under a brute force external attack. The migration required that we receive the users passwords. These would, of course, be reset after...
Service Alert
We're experiencing an extra heavy call volume today and it's proving challenging to respond as quickly as normal. It's been brought on by an apparent Microsoft change resulting in unexpected Windows 11 upgrades. These are happening to a number of devices even if...
Breaking news: New protections added to Kinetics KARE Foundation
We have big news for Kinetics customers on our “KARE Foundation” cyber plan. We've added new Browser Cyber-Protection We’ve found an amazing new security tool called ‘Conceal' that provides even more added protection. Cyber-security is all about layers and this one...
Penetration Testing
Penetration testing is important for businesses because it helps them identify and fix security vulnerabilities before they can be exploited by attackers. It can be a significant job as it needs a team of security professionals to simulate a real-world cyberattack....